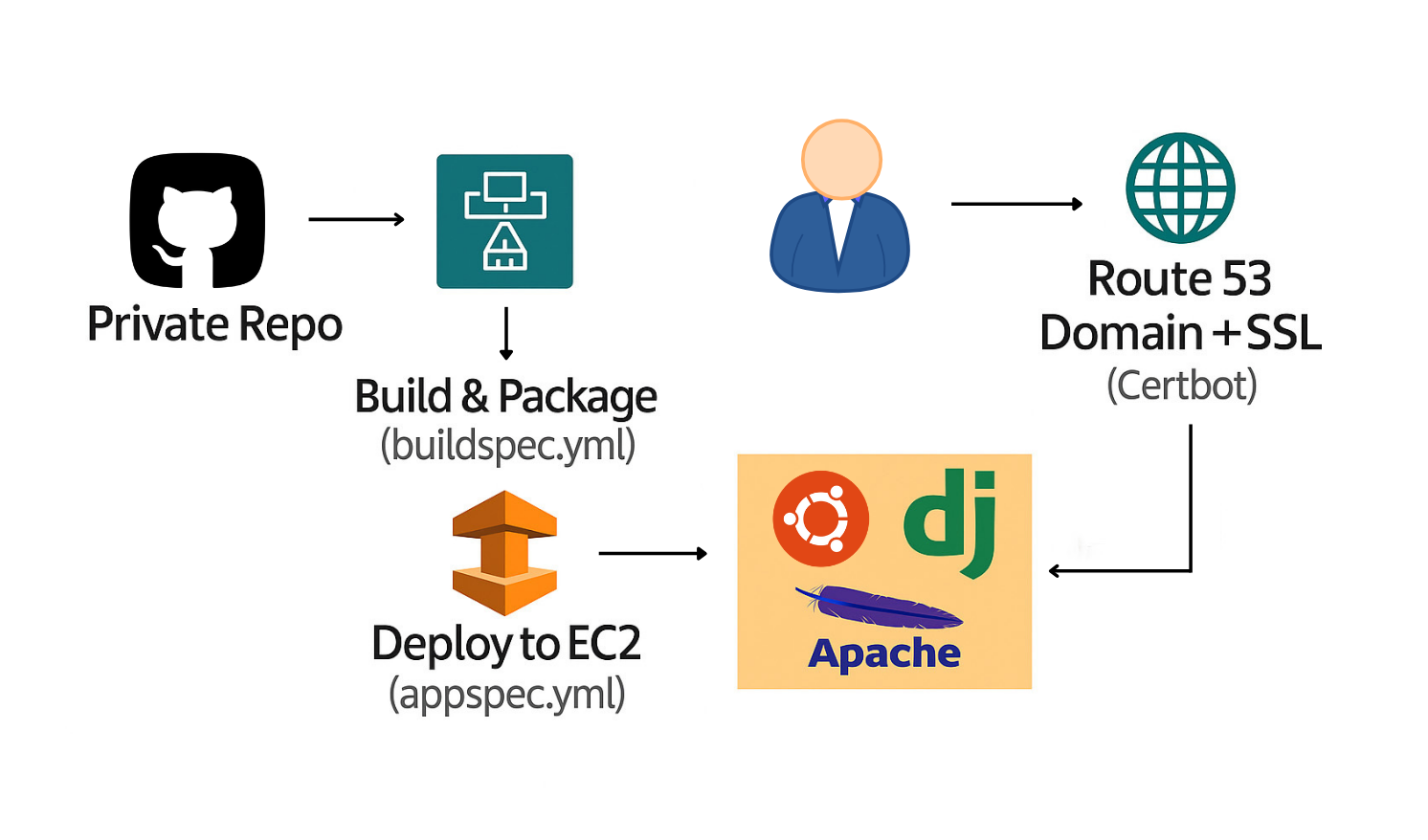
The deployment process begins with building a Django application that connects to an AWS RDS (PostgreSQL) instance for production data. Static assets (CSS, JS) and user-uploaded media are handled within the local project structure. The source code is pushed to a private GitHub repository, and a Personal Access Token (PAT) is generated to allow secure integration with AWS services. On the server side, an EC2 instance running Ubuntu is launched. After system updates and package installations (Python, Git, Apache, mod_wsgi), the app is cloned from GitHub. Apache is configured to serve the Django project using a virtual host file, with custom environment variables injected into the WSGI process.
To enable automated deployments, AWS CodePipeline is used in conjunction with CodeBuild and CodeDeploy. The pipeline is triggered by GitHub webhooks on every push. CodeBuild reads instructions from buildspec.yml, installs dependencies, prepares static files, and packages the application. CodeDeploy then uses appspec.yml and start_application.sh to control the EC2 deployment lifecycle from stopping the server to pulling the latest version, applying updates, and restarting Apache. AWS Secrets Manager is used to store sensitive environment variables (like secret keys and database credentials), which are securely accessed via AWS CLI and injected dynamically into the server using a custom envvars loader.
For production readiness, a custom domain is purchased through AWS Route 53 and mapped to the EC2 instance's public IP address using an A record. HTTPS is enabled by installing Certbot on the EC2 instance to generate and auto-renew an SSL/TLS certificate. The Apache configuration is updated to route HTTPS traffic, ensuring encrypted communication between users and the application. This end-to-end CI/CD pipeline provides a secure, automated, and flexible deployment workflow for Django, combining infrastructure control with modern DevOps tooling.